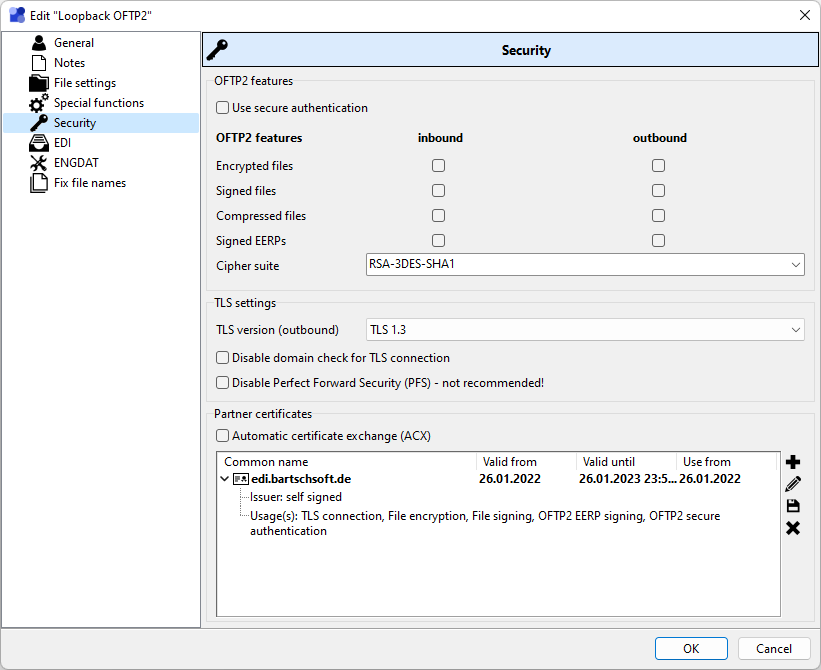
OFTP2 features
Use secure authentication
Both sides authenticate themselves using their certificate in addition to Odette identifier and Odette passwords.
OFTP2 features
•Encrypted files - Specifies if encrypted files are received and if files should get encrypted before being sent. The ciphersuite to use can be chosen further down. Encryption is used to secure access to the content of transmitted files.
•Signed files - Signing of files authenticates their origin and validates that the file wasn't altered during transmission. Outgoing files will be signed before they are sent, for incoming files !MC5 tries to validate the signature after receiving them. The result of the validation will be logged in the !MC5 protocol.
•Compressed files - Specifies if files should get compressed before being encrypted or signed. File compression can reduce transmission times due to smaller files.
•Signed EERPs - Signing of end to end responses assures their origin authenticity and data integrity.
•Cipher suite - The cipher suite used for OFTP2 features.
Security features have to match your partners requirements. Activate any of these features only if required by the respective partner or if you want to require them from him. If e.g. encrypted file transmission is activated and an unencrypted file shall get sent, encryption has to get deactivated before sending. Security features are set on a partner base not a transmission base.
TLS settings
TLS version
The TLS version to be used, when connecting to this partner. A higher version equals higher security.
Disable domain check for TLS connection
When establishing a TLS connection to an OFTP2 partner !MC5 tests if the domain name contained in the received certificate matches the host specified in the field General / IP address. If both don't match, the connection gets closed. Some partners require to connect to hosts or IP addresses that don't match the domain name contained in their certificate. For those partners, this option has to be activated in order to actively connect to them. When the domain check is disabled the received certificate has to match exactly the certificate specified for the usage TLS authentication.
Adding partner certificates
In the box Partner certificates one or more partner certificates can be added. For each certificate usages have to be specified. For which usages certificates are required depends on which OFTP2 features are activated. One certificate can be used for all usages or different certificates for different usages. If multiple certificates are specified for the same usage(s), !MC5 automatically uses the newest certificate.
Automatic certificate exchange
!MC5 supports automatic certificate exchange (complying to the OFTP2 Implementation Guidelines). To use the automatic certificate exchange with a partner, the option Automatic certificate exchange has to be enabled. Also the partner has to support the automatic exchange.